Phishing is an exploit where cyber-criminals assume the identity of a recognized company to hook recipients into revealing credentials to accounts, personally identifiable information, or to open attachments that download dangerous malware, keystroke loggers or ransomware onto your computer and network. Familiar logos, colors, page styles and formatting, along with email addresses and domains are the reassuring bait that lures the recipient to click that link in phishing emails. We hear from victims, “but the email was from (fill in the blank): DropBox, Microsoft, PayPal, Adobe, Google, LinkedIn, my bank or even the IRS or FBI.
Hackers use aggressive subjects such as Security Alert, UPS Delivery Attempted, Unusual Account Activity, Mail Suspension Notice, Response Required, Immediate Password Change Required and the like. Familiarity, anxiety or borderline panic due to a threatening subject distracts busy recipients from taking the time to consider the validity of a message before reacting reflexively to open the link that leads them down the phishing scam rabbit hole.
Interesting Fact – Phishing is a play on the word “fishing” which arose among 1990’s self-named hackers assailing phone systems who were known as “Phone Phreakers”.
Spear Phishing is an escalated phishing attack that is a carefully crafted and precisely targeted attack where the bad guys research an organization, its employees, clients and structure to devise messages with familiar sender addresses, subject lines, artwork, signature blocks and message bodies that are very difficult to discern as fake. Hackers often possess entire email threads that originate with your company from which they extract discussion topics to build their attack on.
One hack leads to another. When an associate carelessly concedes access to their poorly secured email account due to an easily guessed password, emailing passwords via unsecured email, or the harvesting of a password from another hacked account that unlocks with the same or similar credential, the bad guys now have a wealth of information to leverage their next attack. They comb contacts, their email addresses, street addresses, phone numbers, spouse’s names, birth dates and more. They read through the emails in search of credentials and pertinent information that will appear so familiar to their next victim that they don’t hesitate to click the link to download the phony document, fill out the required form or open the bogus attachment.
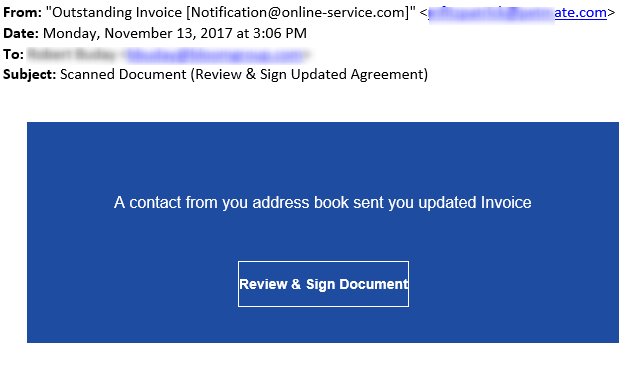
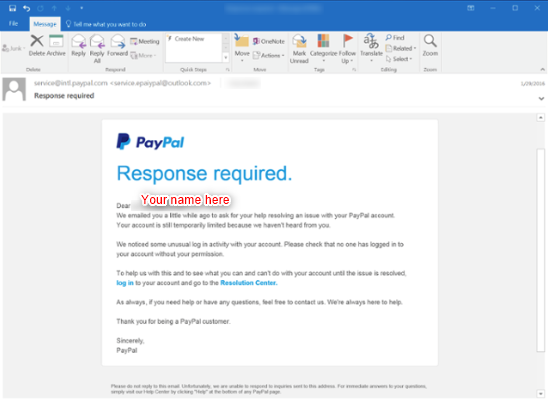
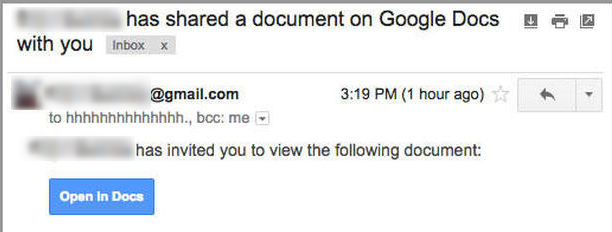
Phishing Examples
The spear phishing attack may appear to come from someone you trust: your boss, co-worker, the HR department, an important client or even one of your awesome IT Administrators. The email style will look the same, the signature block is familiar, and the subject line is topical and relatable.

So, what do you do, how can you tell? My advice is to slow down, be cautious and trust your instincts. If there is something “not quite right” then delay your response while you study the message.
• Examine the hyperlink carefully to see if it matches the purported site. Is it really from DropBox, Microsoft, or Adobe? Hackers will spoof websites with similar URL’s that lead to their own fake sites. • Spelling and poor grammar (Scammer Grammar) are often warnings that the sender is not who they represent themselves to be – “We need you verify again for your account that we are currently send this warning message!” • If you’re not sure, then use your browser to go directly to the site yourself without clicking the email link. • Reply to the sender for verification but keep in mind that if the bad guy has control he may be the one replying “yes it’s me, please hurry up and respond with the requested information”. • Still not sure, pick up the phone, call the sender and speak directly to them for verification. Don’t worry about seeming insecure or overly cautious as there is no such thing when the risks are so high. If they don’t get that, rest assured, one day they will, and it won’t be pretty. • If you can’t verify the source and intention of the sender, then just delete the message. There is nothing, absolutely nothing that can’t be resent. If you don’t response to a valid message you are very likely to hear back from the sender.
• Contact your friendly IT Helpdesk for guidance.
• The IRS, FBI, your bank and software vendors are not going to send you an email requesting your username and password or other sensitive information. • Employ solid network security with multiple layers of protection, Anti-Virus, email security filtering and website filtering.
Remember that the most important and final line of defense for your network is a well-educated end user.













Commentaires